Nethermind
Generate the JWT file
We first need to create a JSON Web Token (JWT) that will allow the execution layer software (Nethermind) and the consensus layer software to talk to each other.
Run the following commands one line at a time to create a folder on the server to store the JWT file and generate the JWT file:
sudo mkdir -p /var/lib/jwtsecret
openssl rand -hex 32 | sudo tee /var/lib/jwtsecret/jwt.hex > /dev/nullWe will be pointing the configuration files of the execution and consensus clients to this JWT file later.
Install dependencies - Unzip, Snappy & the GNU C Library
sudo apt-get update
sudo apt-get install unzip libsnappy-dev libc6-dev libc6 -yDownload Nethermind and configure the service
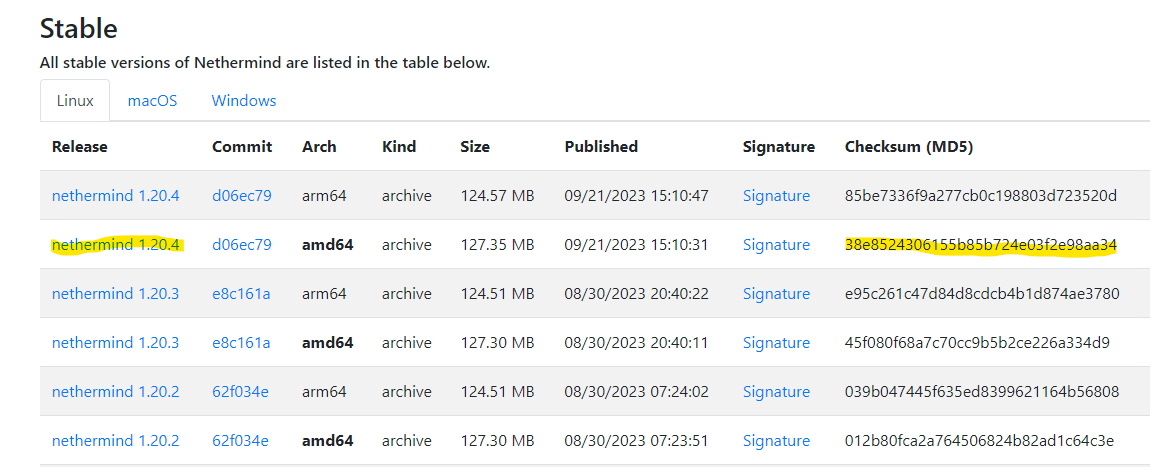
Download the latest version of Nethermind and run the checksum verification process to ensure that the downloaded file has not been tampered with.
cd
curl -LO https://nethdev.blob.core.windows.net/builds/nethermind-1.29.1-dfea5240-linux-x64.zip
echo "21c58995d82163d62bf7ebb78ea5916e nethermind-1.29.1-dfea5240-linux-x64.zip" | md5sum --checkEach downloadable file comes with it's own checksum (see below). Replace the actual checksum and URL of the download link in the code block above.
Make sure to choose the amd64 version. Right click on the linked text and select "copy link address" to get the URL of the download link to curl.
Expected output: Verify output of the checksum verification
If checksum is verified, extract the files and move them into the (/usr/local/bin) directory for neatness and best practice. Then, clean up the duplicated copies.
Create an account (nethermind) without server access for Nethermind to run as a background service. This type of user account will not have root access so it restricts potential attackers to only the Nethermind service in the unlikely event that they manage to infiltrate via a compromised client update.
Create a directory for Nethermind to store the blockchain data of the execution layer. Then set the owner of this directory to nethermind so that this user can read and write to the directory.
Create a systemd configuration file for the Nethermind service to run in the background.
Paste the configuration parameters below into the file:
Once you're done, save with Ctrl+O and Enter, then exit with Ctrl+X. Understand and review your configuration summary below, and amend if needed.
Nethermind configuration summary:
--config: Run the on the Holesky testnet--datadir: The directory for Nethermind to store the blockchain data of the execution layer--JsonRpc.JwtSecretFile: The directory pointing to the JWT secret we generated earlier--Sync.SnapSync: Use Nethermind's snap sync feature. More information here--Network.P2PPort/--Network.DiscoveryPort:Sets the port used for peer-to-peer communication. Defaults to 30303.--JsonRpc.Enabled:Enables the JSON-RPC service on http and websocket. This is so that DVT clients such as the Diva service can connect to your execution client--JsonRpc.Host:Sets the IP address to connect to the JSON RPC service. Use the internal IP address of your device here (check by runningip a) - e.g.192.168.x.x. Defaults to127.0.0.1otherwise--JsonRpc.Port: Sets the port to connect to the JSON RPC service that will be used by the DVT clients. You may choose any unused port number but remember to allow incoming connections into your chosen port in your firewall (ufw) rules. Defaults to 8545--HealthChecks.Enabled:Enables you to test the connection to and health of your Nethermind service using thecurlcommand - e.g.curl http://<Internal_IP_address>:8545/health--Metrics.Enabled: Enable monitoring metrics on the Nethermind service--Metrics.ExposePort:Pushes metrics to your monitoring suite
Start Nethermind
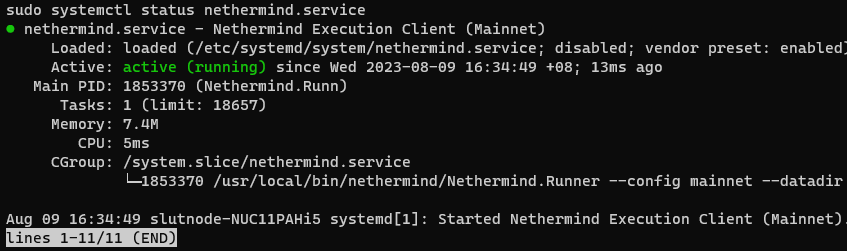
Reload the systemd daemon to register the changes made, start Nethermind, and check its status to make sure its running.
Expected output: The output should say Nethermind is “active (running)”. Press CTRL-C to exit and Nethermind will continue to run. It should take around 12 hours for Nethermind to sync on the Holesky testnet.
Use the following command to check the logs of Nethermind’s syncing process. Watch out for any warnings or errors.
Expected output:
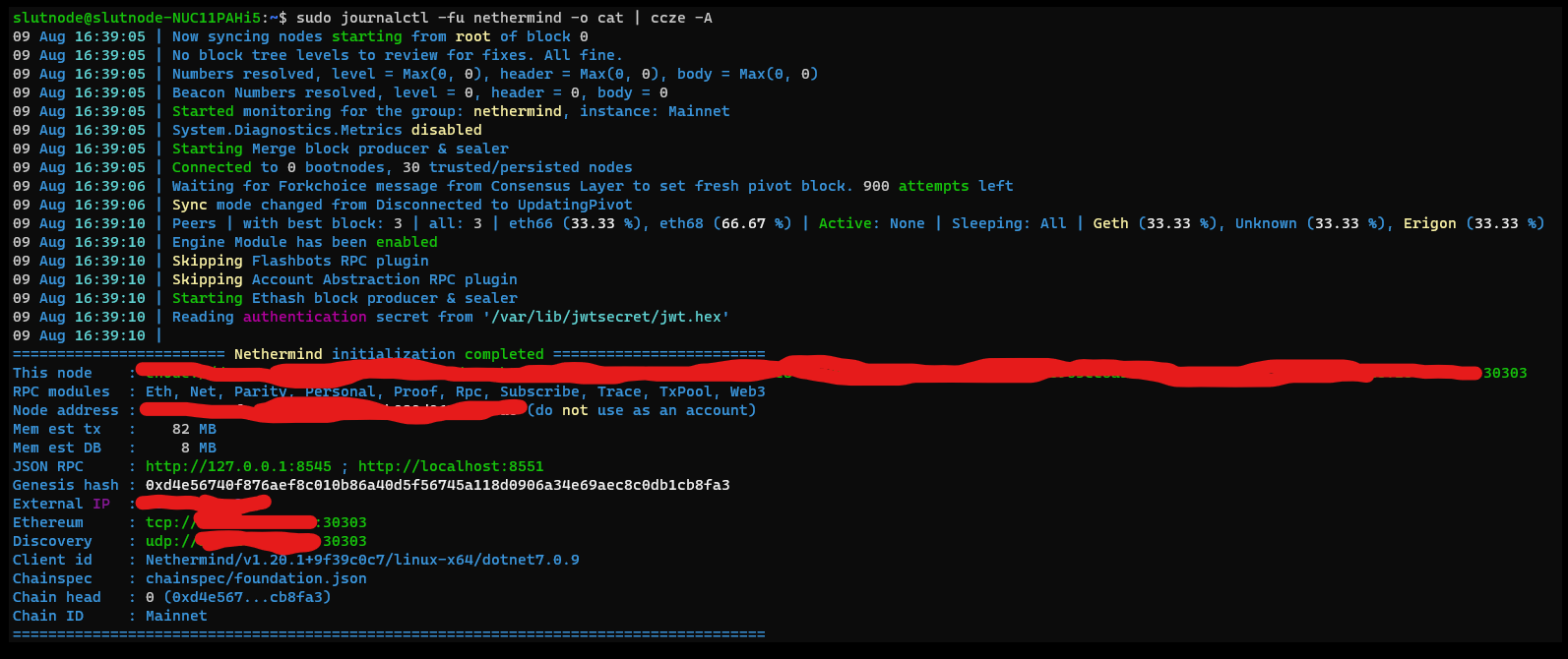
Press CTRL-C to exit.
Note: You will also see the following error related to Pushgateway. This is expected because we have not installed and configured the Pushgateway service used for monitoring at this point.

For more details on interpreting the Nethermind journalctl logs, head here.
If the Nethermind service is running smoothly, we can now enable it to fire up automatically when rebooting the system.
Expected output:
Resources:
Documentation: https://docs.nethermind.io/
Discord: https://discord.gg/MFBrZrGM32
Last updated