Method 2: Configure on separate validator client
Pre-requisites
Make sure you have downloaded the necessary files according to your choice of validator client. Otherwise, revisit the following pages to download and move them into the /usr/local/bin directory.
As we will be using Docker to run the Lodestar VC, we only need to install Docker at this point, and the actual Lodestar binary files will be downloaded when spinning up the Docker container.
Installing dependencies - Docker
The script below performs the following:
Download and run the official Docker installation script
Creates a new user group called "docker"
Adds your current Linux user account to this new docker group
curl -fsSL https://get.docker.com -o get-docker.sh
sudo sh get-docker.sh
sudo groupadd docker
sudo usermod -aG docker $USERLog out and then back in again for the new user group settings to take effect.
exitssh <user>@<IP_address> -p <port_no.> -i <SSH_key> -vCreate new CSM user
sudo useradd --no-create-home --shell /bin/false csm_teku_validatorsudo useradd --no-create-home --shell /bin/false csm_nimbus_validatorsudo useradd --no-create-home --shell /bin/false csm_lodestar_validatorsudo useradd --no-create-home --shell /bin/false csm_lighthouse_validatorsudo useradd --no-create-home --shell /bin/false csm_prysm_validatorBy clearly segregating the users and permissions for separate services in your workflow, this will provide additional safeguards against operational mistakes that can lead to slashing via double signing.
Create new folders for CSM data & keys
Create separate folders, import the CSM validator keys, and set appropriate permissions.
Prepare the CSM validator keystores
1) Create 3 new folders to store the validator client data, validator keystore, and the validator keystore password
2) Copy the validator keystores and it's password file into their respective folders
3) Change the owner of this folder to the teku user
4) Restrict permissions on this new folder such that only the owner is able to read, write, and execute files in this folder
sudo mkdir -p /var/lib/csm_teku_validator/validator_keystores /var/lib/csm_teku_validator/keystore_password
sudo cp ~/validator_keys/<validator_keystore.json> /var/lib/csm_teku_validator/validator_keystores
sudo cp ~/validator_keys/<validator_keystore_password.txt> /var/lib/csm_teku_validator/keystore_password
sudo chown -R csm_teku_validator:csm_teku_validator /var/lib/csm_teku_validator
sudo chmod 700 /var/lib/csm_teku_validatorPrepare the CSM validator keystores
1) Create a new folders to store the validator client data, validator keystore, and the validator keystore password
sudo mkdir -p /var/lib/csm_nimbus_validator2) Run the validator key import process.
sudo /usr/local/bin/nimbus_beacon_node deposits import --data-dir:/var/lib/csm_nimbus_validator/ ~/staking_deposit-cli*/validator_keys3) Change the owner of this new folder to the csm_nimbus_validator user
4) Restrict permissions on this new folder such that only the owner is able to read, write, and execute files in this folder
sudo chown -R csm_nimbus_validator:csm_nimbus_validator /var/lib/csm_nimbus_validator
sudo chmod 700 /var/lib/csm_nimbus_validatorPrepare the validator data directory
1) Create 3 new folders to store the validator client data, validator keystore, and the validator keystore password
2) Copy the validator keystores and it's password file into their respective folders
3) Change the owner of these new folders to the csm_lodestar_validatoruser
4) Restrict permissions on this new folder such that only the owner is able to read, write, and execute files in this folder
5) Retrieve the UID and GID of the csm_lodestar_validator user account to be used in your docker-compose.yml file in the next step
Expected output:
New folders created:
Prepare the validator data directory
1) Create a new folders to store the validator client data, validator keystore, and the validator keystore password
2) Run the validator key import process.
Expected output:

3) Change the owner of this new folder to the csm_lighthouse_validator user
4) Restrict permissions on this new folder such that only the owner is able to read, write, and execute files in this folder
1) Create a new folders to store the validator client data, validator keystore, and the validator keystore password
2) Run the validator key import process.
Note: You will be prompted to accept the terms of use, create a new password for the Prysm wallet, and enter the password of your validator keystore.
Expected output:

3) Create a plain text password file for the Prysm wallet
Enter the password you set during the validator keystore import process. Then, save + exit with CTRL+O, ENTER, CTRL+C.
4) Change the owner of this new folder to the csm_prysm_validator user
5) Restrict permissions on this new folder such that only the owner is able to read, write, and execute files in this folder
Configure the separate VC service
Create a new configuration file for your separate validator client.
Create a systemd configuration file for the Teku Validator Client service to run in the background.
Paste the configuration parameters below into the file:
Once you're done, save with Ctrl+O and Enter, then exit with Ctrl+X. Understand and review your configuration summary below, and amend if needed.
Refer to the native Teku validator client setup section for more information on the other flags used.
Teku VCCreate a systemd configuration file for the Nimbus Validator Client service to run in the background.
Paste the configuration parameters below into the file:
Once you're done, save with Ctrl+O and Enter, then exit with Ctrl+X. Understand and review your configuration summary below, and amend if needed.
Refer to the native Nimbus validator client setup section for more information on the other flags used.
Nimbus VCCreate a new folder for the CSM Lodestar validator client.
Create a docker-compose.yml file in the Lodestar folder.
Paste the following configuration into the docker-compose.yml file. Note: This is similar to the systemd configuration file used in the setup of other clients in this curriculum.
Once you're done, save with Ctrl+O and Enter, then exit with Ctrl+X.
Refer to the native Lodestar validator client setup section for more information on the other flags used.
Lodestar VCCreate a systemd configuration file for the Lighthouse Validator Client service to run in the background.
Paste the configuration parameters below into the file:
Once you're done, save with Ctrl+O and Enter, then exit with Ctrl+X. Understand and review your configuration summary below, and amend if needed.
Refer to the native Lighthouse validator client setup section for more information on the other flags used.
Lighthouse VCCreate a systemd configuration file for the Prysm Validator Client service to run in the background.
Paste the configuration parameters below into the file:
Once you're done, save with Ctrl+O and Enter, then exit with Ctrl+X. Understand and review your configuration summary below, and amend if needed.
Refer to the native Lighthouse validator client setup section for more information on the other flags used.
Prysm VCStart the CSM Validator Client
Create a new configuration file for your separate validator client.
Reload the systemd daemon to register the changes made, start the Teku Validator Client, and check its status to make sure its running.
The output should say the Teku Validator Client is “active (running)”. Press CTRL-C to exit and the Teku Validator Client will continue to run.
Use the following command to check the logs for any warnings or errors:
Expected output:
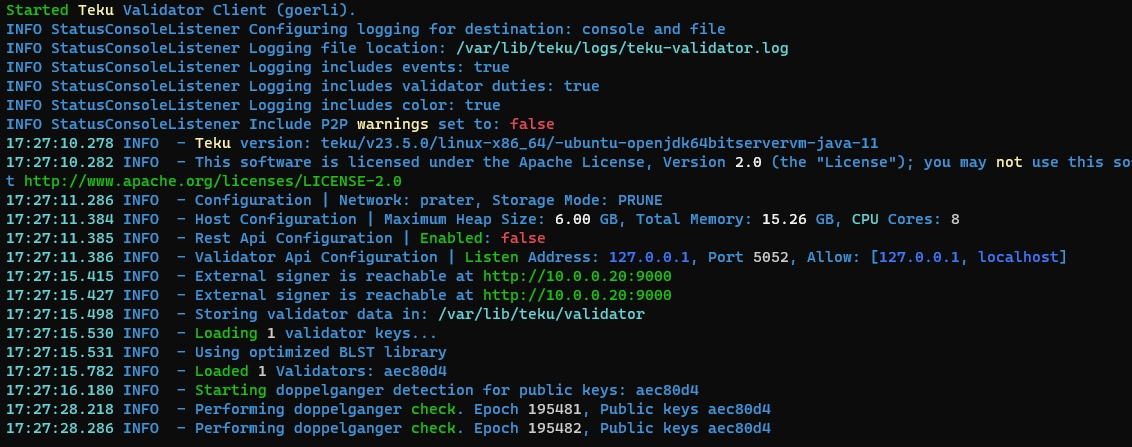
Press CTRL-C to exit.
If the Teku Validator Client service is running smoothly, we can now enable it to fire up automatically when rebooting the system.
Expected output:
Remove duplicates of validator keystores
To prevent configuration mistakes leading to double signing in the future, remove duplicate copies of the validator signing keystores once everything is running smoothly.
Reload the systemd daemon to register the changes made, start the Nimbus Validator Client, and check its status to make sure its running.
The output should say the Nimbus Validator Client is “active (running)”. Press CTRL-C to exit and the Nimbus Validator Client will continue to run.
Use the following command to check the logs for any warnings or errors:
Expected output:

Press CTRL-C to exit.
If the Nimbus Validator Client service is running smoothly, we can now enable it to fire up automatically when rebooting the system.
Expected output:
Remove duplicates of validator keystores
To prevent configuration mistakes leading to double signing in the future, remove duplicate copies of the validator signing keystores once everything is running smoothly.
1) Make sure you are in the same folder as the docker-compose.yml file you created earlier.
2) Start the docker container.
Expected output:
3) Make sure there are no error messages by monitoring the logs for a few minutes.

Remove duplicates of validator keystores
To prevent configuration mistakes leading to double signing in the future, remove duplicate copies of the validator signing keystores once everything is running smoothly.
Reload the systemd daemon to register the changes made, start the Lighthouse Validator Client, and check its status to make sure its running.
The output should say the Lighthouse Validator Client is “active (running)”. Press CTRL-C to exit and the Lighthouse Validator Client will continue to run.
Use the following command to check the logs for any warnings or errors:
Expected output:

Press CTRL-C to exit.
If the Lighthouse Validator Client service is running smoothly, we can now enable it to fire up automatically when rebooting the system.
Expected output:
Remove duplicates of validator keystores
To prevent configuration mistakes leading to double signing in the future, remove duplicate copies of the validator signing keystores once everything is running smoothly.
Reload the systemd daemon to register the changes made, start the Prysm Validator Client, and check its status to make sure its running.
The output should say the Prysm Validator Client is “active (running)”. Press CTRL-C to exit and the Prysm Validator Client will continue to run.
Use the following command to check the logs for any warnings or errors:
Expected output:

Press CTRL-C to exit.
If the Prysm Validator Client service is running smoothly, we can now enable it to fire up automatically when rebooting the system.
Expected output:
Remove duplicates of validator keystores
To prevent configuration mistakes leading to double signing in the future, remove duplicate copies of the validator signing keystores once everything is running smoothly.
Automation Tools
Only 1 instance of ETH Pillar can be running per device. If you are already using ETH Pillar for your own validator node setup, then you will need to use any of the other methods (e.g., ETH Docker) listed in this subpage to import your CSM validator keystores.
Select 4 - Lido CSM Validator Client Only.

Enter your consensus client (beacon node) address. Example: http://127.0.0.1:5052
Verify the fee_recipient address is set to the Lido Execution Layer Rewards Vault.
Generate and import CSM validator keys.
ETH Docker sets the fee_recipient address on the validator key level. Refer to the subpage below, under "Automation Tools".
Resources
Documentation: https://docs.teku.consensys.io/introduction
Discord: https://discord.gg/consensys (Select the Teku channel)
Documentation: https://nimbus.guide/install.html
Discord: https://discord.gg/BWKx5Xta
Git repository: https://github.com/ChainSafe/lodestar-quickstart.git
Documentation: https://chainsafe.github.io/lodestar/
Discord: https://discord.gg/7Gdb4nFh
Documentation: https://lighthouse-book.sigmaprime.io/intro.html
Documentation: https://docs.prylabs.network/docs/getting-started
Discord: https://discord.gg/prysmaticlabs
Last updated